10 April 1404 pm 08:24
Infinity project at the core of Samsung’s mobile sector is trying to protect Galaxy devices against cyber threats; But how?
With the expansion of cyber threats and their increasing complexity, digital security has become more important than ever before. Estimates indicate that the global cost of cybercrime will rise from $ 9.22 trillion in 2024 in the next four years to $ 13.82 trillion in 2028. In this case, the use of devices that operate in a secure ecosystem and receive regular security updates has become an inevitable necessity.
How to protect Galaxy devices against cyber threats?
Samsung has announced that it will provide security updates for its devices for up to seven years from the Galaxy S 24 series. This support is one of the longest security courses among smartphones and allows users to use their devices with high security and security for a longer time.
But how and where do these updates come from and why do they appear regularly on Samsung phones? At the core of Samsung’s mobile sector, there is a confidential project called Infinity that a team of security experts work around the clock. The purpose of the project is to protect users of the Galaxy from cyber threats. Below, we will take a closer look at the different parts of the project.
Discovering unknown threats in cyber space
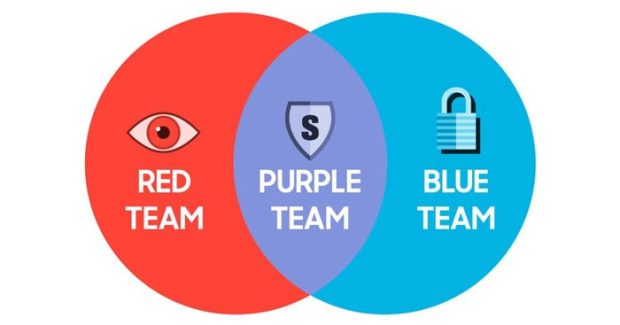
The Cyber Threat Information Team (CTI) is one of the key parts of the Samsung Infinity Confidential Project, which works in collaboration with the Red, Blue and Purple teams. These teams identify and neutralize real threats by going beyond the laboratory. The Red Team is responsible for simulating cyber attacks, the blue team focuses on preventive defense, and the Purple team as a special operation unit plays a defensive and offensive role.
Strategically based in countries such as Vietnam, Poland, Ukraine and Brazil, these specialists are secretly operating and the only sign of their presence is regular security updates in Galaxy devices. By identifying cyber threats and managing risks related to information theft, the CTI team prevents hackers from being controlled and ensures users’ security against advanced attacks.
In addition to securing the Galaxy devices, the CTI team also protects Samsung’s internal infrastructure and defends customer data and confidential information. The team prevents possible abuse of sensitive information by preventing unauthorized access and cyber influence; Because any leakage of confidential information can lead to illegal sales of data or subsequent cyber attacks.
The CTI team is constantly observing the Deep Web and Dark Web to identify threats and implement security measures. These spaces are home to underground markets, where exploites, spies, malware, illegal tools and confidential information are sold. Examination of these environments allows CTI to identify potential threats before cyber attacks and take preventive measures to protect Galaxy users.
The CTI team is led by Justin Choi, the deputy and director of the Samsung Mobile Experience Security Team (MX). With more than twenty years of experience in the US technology industry, he has worked with large financial and technology companies as a cyber security expert and ethical hacker. His expertise in identifying and reducing emerging threats has led to the development of advanced security measures that protect the information and privacy of more than one billion Galaxy users around the world.
Justin Choi, director of the Samsung Infinity project security team, says of the team’s research methods:
Sometimes we simulate real transactions for security research. We carefully monitor the online forums and markets to identify any new and unknown threats that target Galaxy devices. With a deep understanding of hacking and vulnerabilities, we can quickly track the source of any suspicious behavior in the system and threats before it happens.
For example, abnormal requests for excessive access, unexpected behaviors, and communication with unknown servers can be a sign of a potential security breach. In this case, the CTI team tries to identify the origin of the attack, the invaders and their goals by tracking the invasion indicators and to take the necessary steps to prevent any cyber threat.
Ranger, a member of the CTI team who works to protect against hackers’ personal attacks, says of the process of dealing with cyber threats:
When we identify such threats, we work with developers and operators to lock everything and prevent attacks. Even to reduce risk, we communicate with other sectors and security partners through private channels.
In addition, the CTI team examines and analyzes the behavior of the perpetrators. A deep understanding of their motivations and goals can reveal the specific methods of their attack and provide important information to improve and enhance security strategies. These analyzes help the security team design the best solutions to prevent attacks and counter cyber threats more effectively.
Tower, a member of the CTI team, explains in various reasons for cyberattacks, sometimes attacks with financial or political goals; But in some other cases, hackers are only attacking their abilities.
Coping with threats before becoming a real danger
Identifying threats at the right time is of great importance; But having a preventive security policy is just as vital. Samsung’s red and blue teams have been inspired by military methods; Where the red team simulates enemy attacks and the blue team designs defenses to deal with threats. In this way, the red team simulates the hacker attack scenarios and identifies possible weaknesses, while the blue team develops and executes security patch to protect these threats.
These teams specialize in the face of new and unknown attacks, Zero-Day, and prevent unauthorized access or violation of information before hackers abuse vulnerabilities. One of the prominent examples of such violations was Pegasus in 2020, which made an operating system vulnerable to threats.
The Samsung Red Team begins with a careful examination of the Galaxy devices. The team continually tests new features of the devices and identifies and analyzes new vulnerabilities. Their goal is to predict possible cyber threats for users. After extensive investigations, if a serious risk to users’ security is identified, the red team begins to discover Zero-Day vulnerabilities.
Top experts to ensure users’ security
The Purple Team in Samsung acts as a multipurpose unit as a striker and a defender to ensure the security of the vital parts and key features of the Galaxy. As the team’s name implies, it is a combination of red and blue team skills, but its distinction is deeper than the specific security measures of mobile devices that distinguish it from other teams.
Speaking, a member of the Samsung Purple Team, explains the role of the team:
Samsung is working with foreign security researchers to identify vulnerabilities; But our deep knowledge of Galaxy systems allows us to target potential weaknesses with greater effectiveness and effectiveness.
Oracle, another member of the purple team, believes that the better you know a system, the greater your ability to protect it.
The Samsung Purple Team is in particular to solve issues that none of the other teams can handle. These include defining new security requirements, designs and features. However, the mission of the team is not limited to keeping the Galaxy Knox security and security platform. Samsung also provides security consultations and specialized solutions to chips and network services providers. As a leader in hardware production, the company is able to use its widespread security innovations and secure its supply chain completely. As such, Galaxy machines also help to strengthen the security of the next generation of chips.
It may be surprising that there are always technical motivations behind these efforts. Members of the Purple team work with a sense of responsibility and commitment to protect users and enjoy identifying and eliminating vulnerabilities. Oracle, a team member, points out that I am not just; My family and friends also use Galaxy; So we have to secure it in the best possible way.
Entering the Samsung Purple team requires prominent technical capabilities, but this is not the only condition. Applicants must also prove their strong and ethical personality, as the vulnerabilities identified by the team can make a profit for the individual if abuse.
Choi states that team members must be morally solid and have high responsibility. They must prioritize users’ interests over their personal interests.
Protect users’ security with Galaxy Defense System
CTI, Red, Blue and Purple Teams are part of Samsung’s security strategy for Galaxy devices; But the Samsung Infinity project goes beyond that and manages a variety of applications, including Samsung Mobile Security Rewards Rewards Programs, which in partnership with the widespread security community, explores and enhances the Galaxy’s immune system.
“Encouraging the cooperation of the security community to identify potential vulnerabilities is of great importance, especially in today’s world where cyber attacks are becoming more complex and dangerous every day,” Choi explains. These efforts are in line with Samsung’s long -standing strategy in collaboration with hundreds of partners, including operators, service providers and chip producers. “Having internal experts does not mean that we are ignorant of working with others,” Choi continues. “Having more views allows us to identify vulnerabilities faster and protect users better.”
Now that you realize that these updates are the result of a team that cares about your security, it is best not to ignore them. Any update notification is a symbol of Samsung’s continuous commitment to maintain the security of your data. The next time you encounter an update, don’t doubt. Press the “Installation” button and continue to live in your online world safely; Because a complete team protects your security.
(tagstotranslate) cyber security
RCO NEWS