The transparency of transactions in the China block means losing users’ privacy. Tornado Cash has emerged as a new solution for anonymous digital currency transaction in Ethereum. In this article, we will carefully examine the performance of the Tornado Cash, its advantages and disadvantages, the legal and future status of this protocol. If you are looking for a deeper understanding of Privacy’s privacy tools in China’s block, don’t miss this article.
What is Tornado Cash?
Tornado Cash (Tornado Cash) A decentralized protocol based on the Ethereum China Block (Ethereum) with the aim of Anonymity of digital currency transactions Developed. This protocol using advanced technology Proof of zero knowledge (ZK-SNARK) Allows the tokens to mix, or the “mix” to eliminate the link between the source address and the transaction destination.
Unlike many concentrated mixers, Tornadoosh is completely without the need for trust, and users can increase privacy in the Ethereum network without dependence on a third party. This protocol guarantees the security and immutability of the operation, relying on smart contracts.
Developer and developer team
Tornado Cash was launched by a group of China Block developers in year 6 whose main figures include Alexey PertSev, Roman Semenov and Roman Storm. Focusing on China’s block privacy, the team designed a protocol that allows users to make their transactions anonymously.
Roman Semnov, as one of the co -founders, had previously developed privacy projects. The Tornadoksh team was decentralized and open -minded, and many of its updates were managed through the decentralized PA (DAO).
Tornado history
The Tornadoksh project was launched in year 6, and from the very beginning, due to the focus on anonymous digital currency transaction in the China Ethereum block, it attracted the attention of many Privacy in the field of privacy. The initial version was released in collaboration with a team of security and encryption developers and was soon developed as one of the most popular digital currency mixing tools in the web space and other networks.
Read more: What is Web 2
On August 6, the US Treasury Department (August) (August 1) listed the Tornado Kush for money laundering due to the widespread use of North Korean government hackers, especially the Lazarus group. Following this decision, the official project website was blocked and its gate reservoir was blocked; Even one of the main developers, a portfolio, was arrested in the Netherlands.
In the following year, Roman Storm and Roman Semnov also encountered charges including violations of anti -laundry laws (AML) and aid to cyber criminals. Also in May (May 1), an attack on the Tornado Dao Governance infrastructure led to the loss of the project treasury control, which led to serious security concerns. Finally, Roman Strom’s trial takes place in July.
How does Tornadoosh work?
Using advanced encryption technologies, the Tornadoksh protocol allows users to move their digital assets anonymously. Unlike conventional transactions on the Ethereum network, which are generally traced to the network, the Tornadoksh, with a technique called “Transactions,” removes users’ financial footprints. In this section of the article we will explain how the Tornado Cash works.
The process of composition and liquidity pools
Transaction anonymity in the Tornadoosh is based on the Mixing process or the composition of transactions. In this way, users will first deposit money into a Smart Contract. It then subscribes to a Liquidity Pool. Over time, the user can harvest the same value with a different address, without a clear connection between the deposit address and the harvest.
The role of intelligent contracts and the concept of non -change
Tornado Cash is a decentralized program (DAPP) running on the Ethereum network through smart contracts. Since the code of these contracts is deployed on the China block, they are not changeable. Immutability makes it even unable to change the protocol performance or have specific access to transactions. This has been one of the main reasons for legal disputes around the project.
Technology to proof of zero knowledge and its importance in privacy
At the heart of the Tornadoksh Protocol is an advanced technology called Zk-Snark. This technique allows users to prove that they are allowed to withdraw money without the need to disclose information about the initial transaction. This structure causes the bond between the deposit and the harvest completely eliminated.
How to provide privacy and security in Tornado
To maintain security, users receive a private note that acts as a private key to harvest when depositing. Also, mechanisms such as Merkle Tree and nullifier are designed to prevent the same transaction from re -harvesting.
These features, along with the use of Relayers to hide the user’s address at harvest time, have made the Tornadoosh a digital currency mixer and one of the most powerful anonymous tools in China’s block.
Tornado Keys and Benefits
As a leading protocol in protecting the privacy of China’s block, Tornadoosh offers numerous features and benefits that distinguish it from other similar tools. These features are based on advanced technologies and decentralized design of this protocol.
- Increased privacy in transactions: Proof of zero knowledge in Tornado Cash enables completely anonymous transactions. This feature disconnects the connection between the sender’s address and makes it impossible to track money in the China Ethereum block.
- Using Zero Knowledge Proof (ZK-SNARK): This technology allows users to prove its accuracy without disclosing the details of the transaction. ZK-SNARK in Tornado Cash guarantees that sensitive information such as the amount of money or identity of the parties remains secret.
- Anonymity Mining: Anonymity Mining: The Tornadoosh provides a system for rewarding users who, by depositing money into the liquidity pools and participating in the composition process, Torn token. This feature encourages users to use the protocol.
- Decentralized and unchanged: The Tornado Smart Contracts are decentralized and are immutable after deployment. This feature attracts users’ trust and eliminates interference.
- Support for fixed values in pools: The Tornadoksh uses fixed values (such as 1.2, 2, 2 or 3 ether) in liquidity pools that enhance anonymity and make China’s block analysis more difficult.
- Support for different currencies: In the original version of the Tornadoosh, currencies such as ETH, DAI, USDC and WBTC are supported. Version of this protocol has also been developed for other networks.
These features have made Tornado Cash a powerful tool for users seeking to protect the privacy of the China Block; However, the legal challenges have limited its use.
What is Torn’s digital currency?
The Torn Digital Currency is a Tornado-Kash protocol that acts as an ERC-1 token on the Ethereum Network. Designed with a fixed supply and is used to decentralize the protocol and encourage users to participate in the Tornado Ecosystem. Torn allows users to contribute to protocol decisions and benefit from its financial benefits.
Torn token use
Torn currency has several applications in the Tournament Ecosystem, which includes:
- Protocol Management: Torn owners can submit new suggestions to improve the protocol and participate in strategic decisions.
- Encourage users: Torn is distributed as a reward for participating in the anonymous process, which is an incentive to actively use the protocol.
- Trading in the market: Torn is tradable in decentralized and centralized currency exchanges and its value depends on the demand and performance of the protocol.
- Access to Advanced Features: Some specific functions of the protocol may require maintenance or use of Torn.
Tokenomics torn
Token Torn, Tornado Kash’s token, has a maximum supply of 2 million units. The following table shows the allocation and token status. The structure of allocation helps to gradually liberate tokens and encourage users to participate.
| Name | Total allocation | Released | Locked |
|---|---|---|---|
| Governance | % 1 | % 2.3 | % 2.3 |
| Team and investors | % 1 | % 4.3 | – |
| Anonymous extraction | % 1 | % 1 | – |
| Idraps | % 1 | % 1 | – |
Different Services and Services
Tornado Cash is not just a simple digital currency mixer to hide transactions; This protocol is a decentralized ecosystem with many components that include the governance structure, the monetization opportunities, and the technical tools. Users in the Tornadoosh are not only able to do private transactions; Rather, they are involved in its development and administration. The most important side parts of the Tornado Cash are:
- Torn token sticker: Users can handle their Torn currency in a special contract. This process enables them to vote for the sovereignty of the protocol, while supporting the resources deposited in the development of the protocol.
- Participation in DAO voters: Protocol rule is performed through a DAO. Torn token owners can vote on key changes such as technical parameters, capital allocation, or the development of new versions.
- Earn a rewardA: Some Tornado Cash versions had incentive mechanisms such as Liquidity Mining that users received in exchange for deposit and participation in the pools. Participation in sticing and voting can also be rewarded.
- Railers (Relayers): Railers are services that help users harvest their funds anonymously. Users can make their transactions without direct connection to the original address by paying the fees to the Railers; This increases privacy.
The combination of these components has made the Tornado Cash a full -fledged privacy protocol and decentralized governance.
Is the Tornado Cut safe?
ZK-Snark in Tornado Cash and Unchanged Smart Contracts provides a high level of privacy and security for transactions. This protocol makes it impossible to track transactions by disconnection between the transmitter and the receiver and the use of liquidity pools. However, there are also possible risks and abuses.
In May, a security hack allowed the attackers to seize some smart contracts that led to concerns about infrastructure vulnerabilities. In addition, hackers, such as the Lazarus group, for money laundering, have exposed the protocol to legal charges.
The US Treasury Department’s sanctions and developers’ arrest have also increased the risks related to the use of the service. Therefore, users should use the Tornado Cash with full awareness of these risks.
Tutorial
Tornado is a tool for anonymity of transactions in the China Ethereum block. In this section of the article, we will explain the tutorial on the use of Tornado Cash and the anonymity of transaction transaction in the Tornadoosh.
Login to DIAP
First, remember to use the Tornadoksh you must use an IP change tool and then visit the official Tornadocash website. Click the Launch App to start working with the Tornado.

Deposit
Click the Connect and connect your Metamsk wallet to the Tornadoosh. In the DiP, deposit the desired amount (such as 0.5, 2, 2 or 3 ether) from your wallet into one of the Tornado Cash Pools. This process is managed by a smart contract. After the transaction is confirmed, your money will be added to the pool.
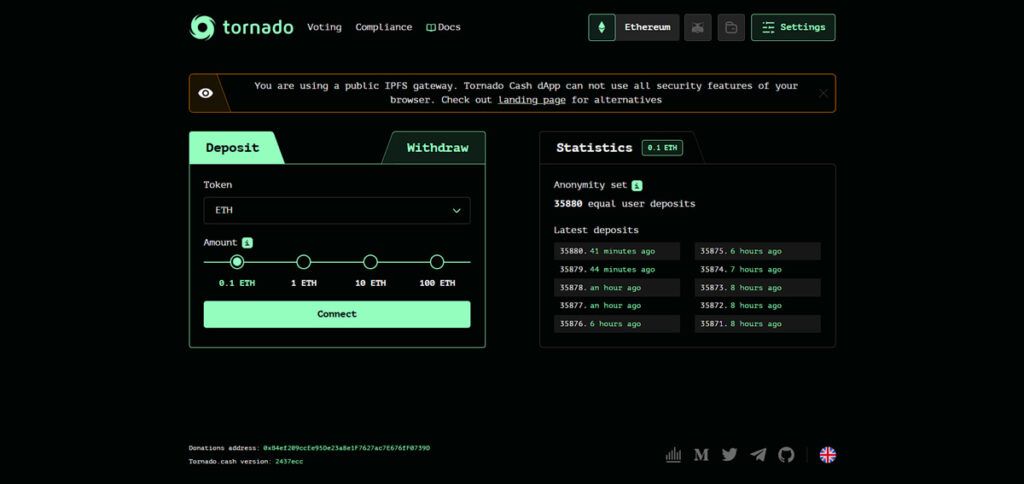
Creating the key
After depositing, you receive a private note that contains a encrypted key. This key is essential for removing funds. Save it in a safe place; Because without it you can’t harvest your funds.
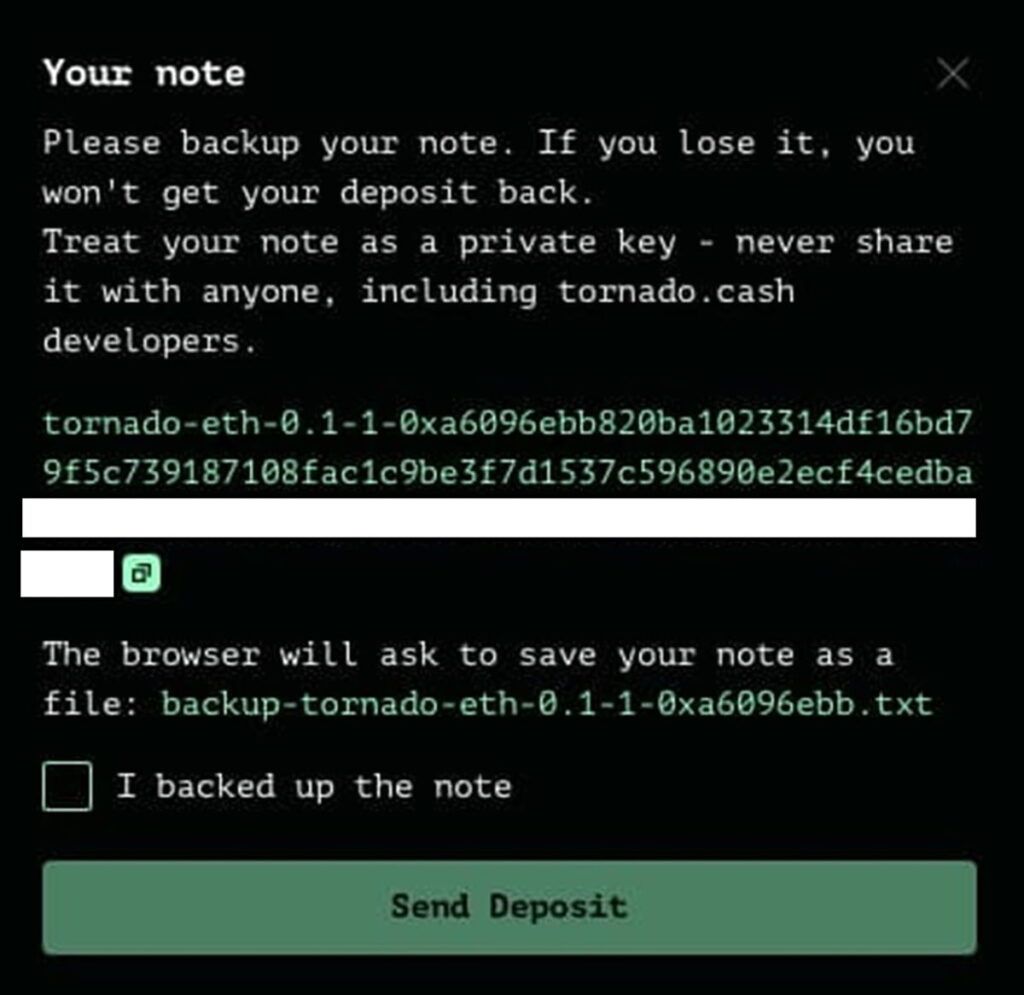
Then click on the “Setup Account” option on the user’s dashboard.
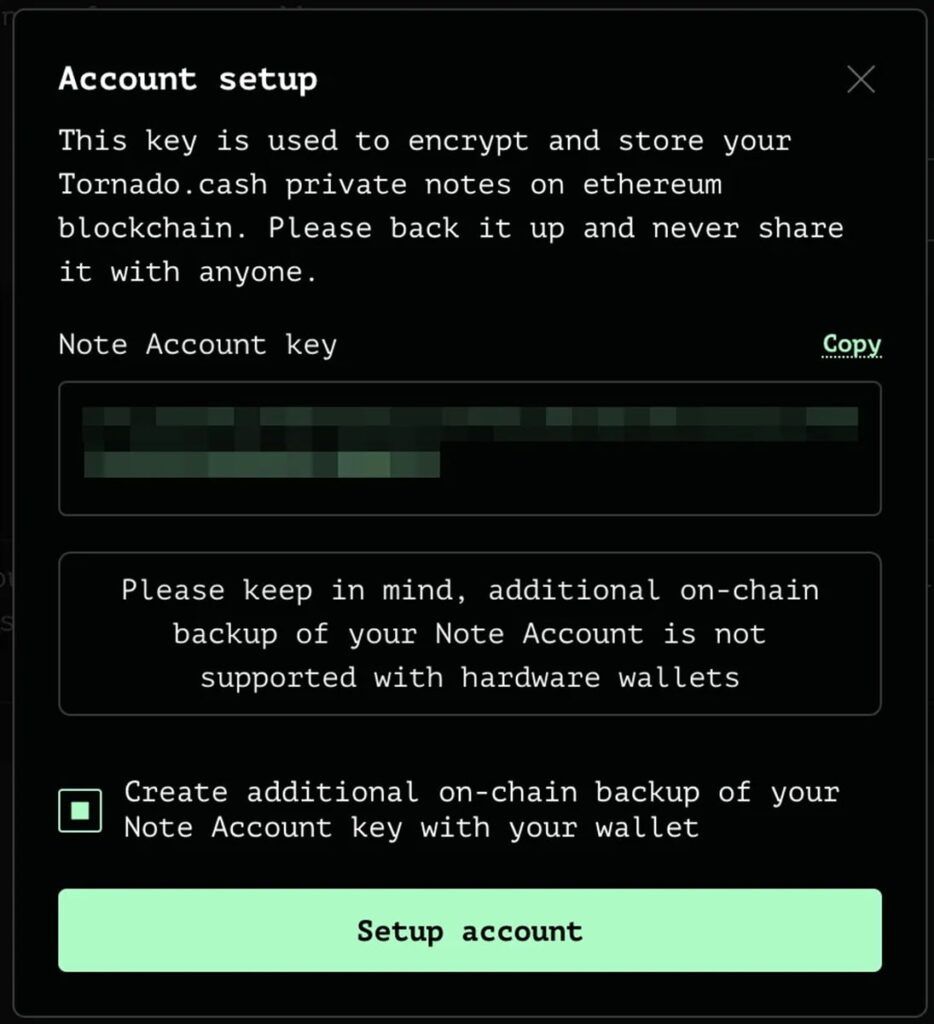
Be sure to back up your information securely. The Note Account key is very important and has a similar role to the private key in the Ethereum. This key is used to encrypt all your private notes.
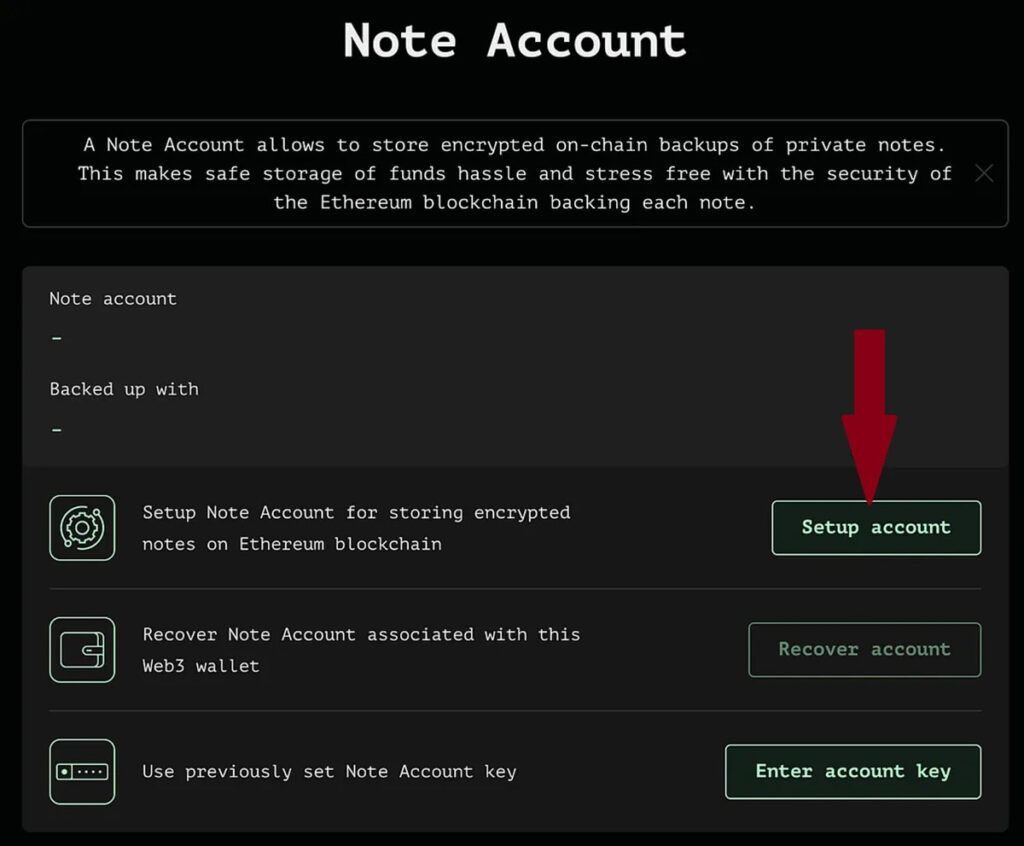
Note: If you do not want to save your Note Key support version, you can uncheck the “Create Additional On-Class Backup of Your Note Account Key with Your Wallet”.
The combination of funds in the pool
Your funds in the liquidity pool are combined with other users’ assets. This process uses ZK-Snark technology to disconnect the link between the deposit and harvesting address and guarantee anonymity.
Harvest
Enter your private note in the DIAP to withdraw (withdraw). You can use a new address or through Relayers to increase anonymity. A small fee is paid to the Reiller to make the transaction without connecting to the main address.
By following these steps, you can do an anonymous transaction in the Tornado, but always consider legal and security risks.
Methods of enhancing security and anonymity in Tornado
For safe and anonymous use of the Tornado Cash, observing the following can enhance the privacy and security of users:
- Use IP or Tour Browser Tool: To hide the IP address, use a valid IP change tool or a tour browser. This prevents tracking your activities by Internet providers or regulatory agencies.
- Secure Save Private Note (Secret Note)A: The private note you receive when depositing is essential for removing money. Keep it in a safe and offline place (such as paper or cold storage) and avoid storage in the cloud.
- Clear browser data: After the transaction, delete your browser’s cache and cookies so that no trace of your activity in the Tornado DiPus will remain.
- Use new addresses to harvest: To increase the anonymity, remove the funds to the new and unrelated address with the address. The use of relics also makes this process safer.
- Avoid Patternsable Patterns: Refrain from depositing and repeatedly withdrawn with specified patterns; Because it may make it easier for China’s block analysis to track.
Tornado -Kashi networks
The Tornado Cash was originally designed for the Ethereum Network, but later expanded to other EVM -compatible clicks to provide more access and flexibility.
Ethereum
Tornado Cash was implemented on the China block because of its unique features such as high numbers, ERC-20 token, strong security and support for smart contracts. Ethereum, as a decentralized platform, enables the implementation of unchanged Tornado Tournament smart contracts that are essential for the privacy and anonymity of transactions. The large number of Ethereum users also guarantee the high liquidity of the Tornado Pools.
Read more: How does Ethereum work
Ethereum -compatible networking networks
To increase access, the Tornado Cash expanded to EVM -compatible networks such as BSC, Paligant, and Aptimism. These networks support smart contracts similar to Ethereum and have less transaction costs that make the use of Tornado Case more affordable.
Legal challenges and sanctions of the Tornado
Tornado Cash has faced serious legal challenges since its operation. The US Treasury (OFAC) has boycotted the protocol for the widespread use of hackers and cyber groups such as Lazarus for money laundering and bypassing anti -laundry laws (AML) and customer identification (KYC). For this reason, access to the Tornado Cash site has been banned for US users and many other countries.
The sanctions have blocked the official Tornado Kash site, suspension of the project’s gate tank, and eventually arresting some of its developers in Europe, including a portfolio in the Netherlands. There were also heavy allegations against Roman Storm and Roman Semnov in year 6, indicating legal pressure on the project.
Despite these challenges, Tornado Kash is still one of the leading privacy platforms in China’s block space, but the legal and security risks of its use should not be overlooked.
Future Road Map and Tornado Kash
Tornado Cash has not released an official and transparent roadmap; This is related to the decentralized nature and its legal challenges. However, the protocol is still seeking to improve its privacy technologies in China and expand its services.
Tornado Cash developers have focused on enhancing smart contracts and increasing adaptation to Chinese block networks. Collaborations with Defi projects and decentralized platforms to integrate Tornado Cash services, such as the use of liquidity pools in other protocols, have been introduced in the past.
These mergers can increase access to anonymous tools. Despite sanctions and restrictions, the Tornado Kashi community continues to operate through the decentralized PA and offers suggestions for improving the protocol. The future of Tornado Cash depends on its ability to manage legal challenges and develop new technologies.
Frequently asked questions
Tornadoosh is a decentralized protocol in Ethereum that, using ZK-Snark’s anonymous transaction, enhances the privacy of users in public folds using ZK-Snark technology.
This protocol, with ZK-SNARK technology and the combination of funds in the liquidity pools, discontinue the relationship between the transmitter and the receiver and make the transactions inaccessible.
The use of Tornado Cash in some countries, such as the US, is unlawful because of Because it is used in money laundering and illegal activities.
Tornado Kash has high security with ZK-Snark and smart contracts, but the hacking of the year and legal risks have made it risky.
The US Treasury (OFC) boycotted Tornado Cash in the year for the use of hackers (such as Lazarus) for money laundering and lack of AML/KYC controls.
The Tornado Cash uses ZK-SNARK, decentralized intelligent contracts and Torn token for sovereignty, which is different from centralized or easier mixers.
Conclusion
As a decentralized mixer, Tornado Cash offers a powerful strategy for privacy in the China Ethereum block. Using ZK-SNARK technology and smart contracts, this protocol makes it possible for anonymous transactions. Although features such as anonymous mining and Torn token have increased its appeal, legal challenges, such as the Sanctions of ATAC and the detention of developers, have created restrictions.
Users should use this tool with awareness of security and legal risks. Tornado Cash is an example of the confrontation between privacy and regulations in the China block world whose future depends on legal and technical developments.
RCO NEWS