Solana developers and credentials together were able to eliminate a critical security vulnerability. However, this rapid correction has been accompanied by criticism of network focusing. The Solana Foundation has confirmed that a zero -day vulnerability that allowed the attacker to multiply and even remove them from the user’s account has been resolved.
The report was first released by the Salana Foundation on May 5. The report said that the Solana security vulnerability, first identified on April 7, could allow the attacker to create an invalid proof that affects the token-22 confidential tokens that provide privacy capability in Solana. According to the Foundation, no well -known exploitation of this vulnerability has been carried out and Sulana’s validation has accepted the modified version.
Solana’s security vulnerability influenced token-22 confidential token
The Solana Foundation said the Solana security vulnerability is related to the two Token-20122 and ZK Elgamal Proof. Token-20122 processs the original program logic for token and account management, while the ZK Elgamal Proof is used to verify zero-knowledge proofs to accurately display accounts.
According to the Foundation, some algebraic components in the process of producing the Fiat-Schamir Transformation Text that specify how the public random provers produce using the encryption hash function were removed from hashs. This defect could allow the attacker to multiply and steal the token-22 confidential tokens by making a fake proof that passes through the confirmation.
This Solana security vulnerability was first identified on April 5, and two patchs were presented to solve the problem. A great majority of Slana’s validation accepted these patches about two days later. Solana developers, including Anza, FireDancer and Jito, played a key role in modifying the vulnerability. In addition to these companies, asymmetric Research, Neodyme and Ottersec played an important role in removing this vulnerability.
Read on Digino:
Slana Price Stabilization; Is there a price leap?
The assets are safe, but users are still worried!
The Solana Foundation confirmed that all assets have remained safe. However, despite the reforms, users are concerned about it. In fact, how the Salana Foundation’s confidential look at this has raised concerns about concentrations by some members of the Crypto community.
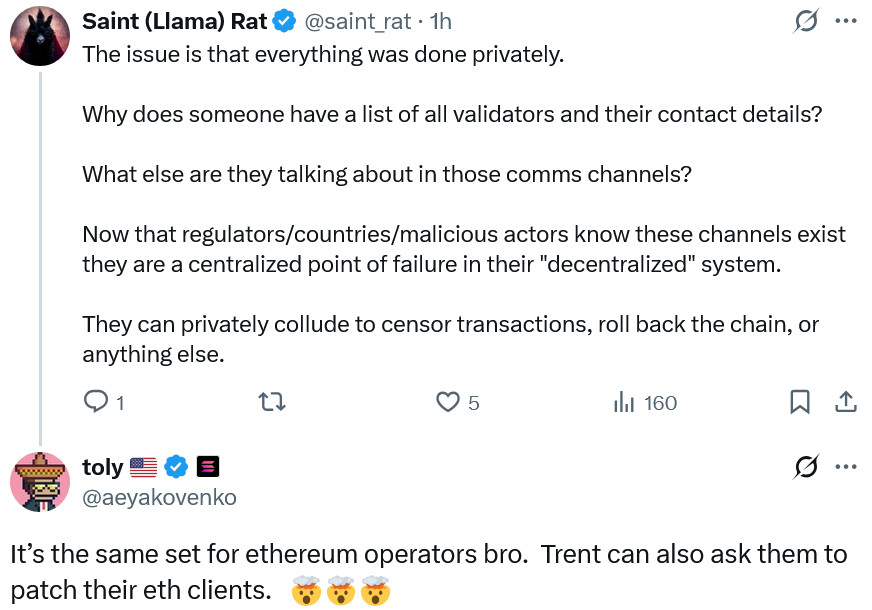
For example, one of the Curve Finance participants has raised concerns about the proximity of the Solana Foundation to validation. He believes why no one has a list of all the validates and their contact information? Under such circumstances, people may collide and censor or censor the transactions or back the chain.
Anatolia Yakonko, CEO of Solana Labs, did not directly reject the claims. However, the members of the Ethereum community could also coordinate to solve a similar security bug. To prove his claim, Yakonko added that more than 5 % of the Ethereum network validation are also controlled by encryption currency exchanges or sticker operators such as LIDO.
In August, the Solana Foundation and the network validity were once again resolved another critical vulnerability. At that time, the executive director of the Foundation, Dan Albert, stated that the ability to coordinate a patch does not mean Slana’s focus.
One member of the community: Ethereum has no such problem!
Ryan Berkmans, a member of the Ethereum community, rejected the claims that Ethereum also rejected the issues of concentration similar to Sulana. He said that Ethereum has enough variety in client software. Berkemans said the most widely used Ethereum client, Geth, has only 5 % market share in most cases. This is while Slana has only one client ready to use in production called Agave. He added that Zero Day bugs in only clients are practically protocol bugs. If you change the client program, you have changed the protocol yourself. The client is the protocol itself.
Final speech
Solana plans to launch a new client called FireDancer in the next few months. It is expected to improve the strength and stability of the network with this client. However, Berkmanz said that so that Slana needs three clients in order to be decentralized enough to be decentralized. What do you think about Solana’s security vulnerability?
RCO NEWS