Many people come into the world of digital currencies with the notion that bitcoin is completely anonymous. But in fact, bitcoin is not anonymous, but pseudonymous. Bitcoin wallet addresses can be tracked and linked to real identities through advanced analysis. In response to this challenge, tools called Bitcoin Mixer (Bitcoin Mixer) Or Tumbler (tumbler) They have emerged.
But what is the bitcoin mixer? How can we use it? Which category of users is suitable for? What are the challenges and risks? Is it legal? These are the questions we are going to answer in this article.
What is a bitcoin mixer?
Bitcoin Mixer (Bitcoin Mixer) It is a third -party software or service designed to hide the traces of digital currency transactions. Its main function is to break the traceable link between the sender’s address (input) and the recipient’s address (output) on the China block. These services are combined in a large black box by receiving funds from multiple users and then sending equivalent sums to the designated purposes.
This process makes it difficult or almost impossible for an external observer to determine who sent it to whom. This process can be likened to a card or use of offshore banking systems in the traditional financial world to hide the source of money.
Does the emergence of mixers defect the bitcoin network?
The emergence and evolution of bitcoin mixers is not a defect in the bitcoin protocol, but a direct response to a fundamental design choice: absolute transparency. White Piper Satoshi Nakamoto prioritized a “needless need” system.
This transparency is a key feature of preventing fraud. Bitcoin was simply the first digital currency to fix the problem of cheating and spending twice, and it was one of the biggest factors in his success. But this amount of transparency sometimes contradicts the global need of humans and businesses in financial privacy.
Users and developers identified the gap and created mixers practically adding a layer of privacy to the transparent bitcoin base layer. This reveals a major philosophical tension in the crypto ecosystem: the confrontation between the ideals of complete transparency and individual financial sovereignty. The mixers are at the point of the confluence of these two ideals.
How does a bitcoin mixer work?
The mechanism of performance of a bitcoin mixer usually contains a three -step process that resembles traditional money laundering, but here is the main purpose (in legitimate applications) privacy.
- Place/ Deposit (Placement/ Deposit): Bitcoin users send their so -called “contaminated” or identifiable to the address that controls the mixer service. At this point, the funds of various users are collected in a large pool.
- Laying/ Mixing: The mixer service mixes the collected funds using complex algorithms. This is a “black box” process in which the bond between inputs and outputs is deliberately broken.
- Integration/ Redistribution: Finally, the mixer sends the equivalent amount of “clean” bitcoins (after deduction of service commission) to new addresses that users have already specified. Returned Quinn has no direct trackable history to the main user’s kins.
Bitcoin Mixers Key Techniques for Hidden
To enhance the efficiency and complicate the tracking process, mixers use several key techniques for hidden:
- Time Delay (Time Delays): Creating a random delay between the time of deposit and harvesting makes transactions more difficult for blockchain analysts. Users can often customize this delay.
- Multiple output addresses (Multiple Output addresses): Users can specify multiple destination wallets and divide the final amount among them, which makes the transaction footprint more.
- Variable Service FEES: Farmes, which usually vary from 0.5% to 5%, are often random or customizable by the user. Higher fees are sometimes accompanied by a more complete and complex mixing process.
- Letter of Guarantee (Letter of Guarantee): Some mixers provide a digital signature message as a transaction degree. If the funds are not returned, this letter can be used to contact the support without having to store user data.
The effectiveness of a mixer is not an absolute software feature, but is directly proportional to the volume and number of its active users. The basic principle of mixing is to hide among the population. If this population is small, China’s block analysis companies can use the analytical methods to deny transactions and rebuild possible links with high confidence.
This creates a paradox of a network effect:
A mixer must be popular for being safe, but its popularity also makes it a bigger goal for hackers and surveillance institutions.
Bitcoin mixer
Bitcoin mixers to Two main models of centralized (Centralized) and decentralized (Decentralized) They are divided, each with different risks and profiles.

Concentrated mixers
These are Custodial Services that a company or private person runs. Users must trust this third party by sending their funds directly to the mixer wallet. The service assumes the custody of the queens, performs the mix internalized, and returns different queens.
- Benefits: They are generally more user -friendly and have simple user interfaces that are suitable for beginners.
- Disadvantages:
- Risk of the opposite side: The user must trust the operator not to steal funds (exit scam or exit scam) or disappear.
- Privacy Risk: The centralized operator has a record of all input and output transactions. He can register these data secretly that he or she may later be hacked, disclosed or seized by law enforcement, and completely eliminates the main purpose of using the mixer.
- Unit failing point: Due to the centralized nature, these services are the main target of hackers, and government officials can easily shut down or seize them.
Decentralized mixers
These are Non-Custodial and P2P (P2P) systems that rely on the source protocols and unnecessary trust protocols. The most prominent technology used in this type of mixers is Coinjoin. Kevin Join is a common transaction in which several users combine their inputs to create a large transaction with multiple outputs.
- Benefits:
- Needless to trust and non -trusted: Users always control their private keys. There is no third party to trust your funds, which eliminates the risk of operator theft.
- Privacy and higher security: Without a central server for registration of transactions, privacy risk is significantly lower. They are also more resistant to closure because of the decentralized nature.
- Disadvantages:
- Complex: Using them can be technically more technically challenging for beginners than the simple interfaces of centralized mixers.
- Population dependence: Their efficacy depends heavily on the number of active participants in a mix. A small pool can endanger privacy.
Comparison of centralized and decentralized bitcoin mixers
The following table shows the differences between concentrated and decentralized mixers.
| Feature | Concentrated mixer | Decentralized mixer |
| Control of funds | Custodial – The user puts his or her funds to a third party. | Non-Custodial-Users maintain their private keys. |
| Trust model | Based on trust in the operator. | Trustless – Security is guaranteed by the protocol. |
| The main risk | Theft by operator, fraud, hacking, registration of logs. | Technical Protocol Risk, China Block Analysis attacks if the participants are low. |
| Privacy | Depends on the honesty of the operator; It is possible to register and disclose the logs. | Higher; Due to the absence of a central entity for registering information. |
| Censorship resistance | Down; Governments can easily seize and block it. | Above; It is more difficult to turn off because of the decentralized nature. |
| Ease of use | Usually simpler and suitable for beginners. | May require more technical knowledge. |
| Main technology | Dedicated algorithms and central servers. | Reserving protocols such as coinjoin. |
| Examples | Cryptomixer.io, Coinomize | Wasabi Wallet, Samourai Wallet (Whirlpool), Joinmarket |
Bitcoin Mixer Applications
The dual nature of the mixers is at the center of all the controversy. These tools are used for both legitimate purposes and for illegal activities.
Some of the legitimate and ethical applications of bitcoin mixers include:
- Financial Privacy: For people who believe that their financial history should not be public, such as the desire to be confidential, these tools are good options.
- Business Protection: Companies may use mixers to hide transactions from competitors, prevent industrial spying related to the supply chain, payroll or investment strategies.
- Anonymous Funds: Supporting political goals or charities without fear of revenge or public oversight.
- Protection in specific jobs: For political activists, journalists, or even ordinary citizens who live in some governments, mixers can be a way to protect their assets against their seizure and their activities against supervision.
In contrast, mixers also have illegal and criminal applications, some of which are here:
- Money Laundry (MONEY LAUNDERING): This is the most infamous use of mixers. Criminals use mixers to wash the proceeds from ransomware attacks, currency exchanges and other cybercrime. For example, the fundamental funds from the Bitmart hack were laundered through the Tornado Cash mixer.
- Darknet Markets Markets: Hide the flow of funds from illegal markets such as Silk Road or Hydra Market in the past.
- TAKE WITH SANCTIONS EVASISION: Government -backed hacker groups, such as the Lazarus Group from North Korea, widely use mixers to laundering funds laundering and escape from international financial sanctions.
How to use a bitcoin mixer?
In this section we will teach you how to use bitcoin mixers.
Of course, we emphasize that the use of a bitcoin mixer like any other operation in the crypto world has a positive and negative zinc. The responsibility for the investigation is the responsibility of the users themselves. Never act without awareness and measure all aspects.
Research and selection
The first step you need to take is to research and choose the best option. When choosing a bitcoin mixer, make sure it does not record the logs, is highly credible, and is well -known in forums like Reddit and Bitcointalk, as well as a long history.
Preparing a clean destination
Never use the money wallet you used to be and can be relevant to your identity. Create a completely new and unused bitcoin wallet to get mixed queens. This is a vital step in operational security (OSPSEC) to prevent your identity re -link.
Secure access
Use the Tor browser to access the mixer website (often available through a .onion address). This prevents your actual IP address from registering your real IP address and adds a layer of privacy at the network level.
Mix parameters configuration
Bitcoin you want to mix is deposited into the address provided by the service. Set a few hours or more to neutralize the time analysis. And specify several outputs from your new wallet to receive funds as smaller and fragmented.
Finalization
Provide the new recipient’s address (s). If the service guarantees as a guarantee, save it safely. This is the only evidence of your transaction if there is a problem. Then confirm the transaction and wait for the mixed queens to arrive. Also note that you will never send funds to a currency exchange that requires identity (KYC) immediately after the mix.
Security alert
Effective use of a mixer is not a simple transaction, but a security protocol. A small mistake, such as reuse of an old wallet or access to a service without TOR, can completely eliminate privacy gains and endanger the user.
The human factor is the weakest ring in this chain. The self -instrument’s self is not enough; It is the user’s discipline and its operational security that determines the real level of privacy.
Bitcoin mixer risks and challenges
This is one of the most important parts of the article. In this section, we introduce the severe risks that users face and explain each.
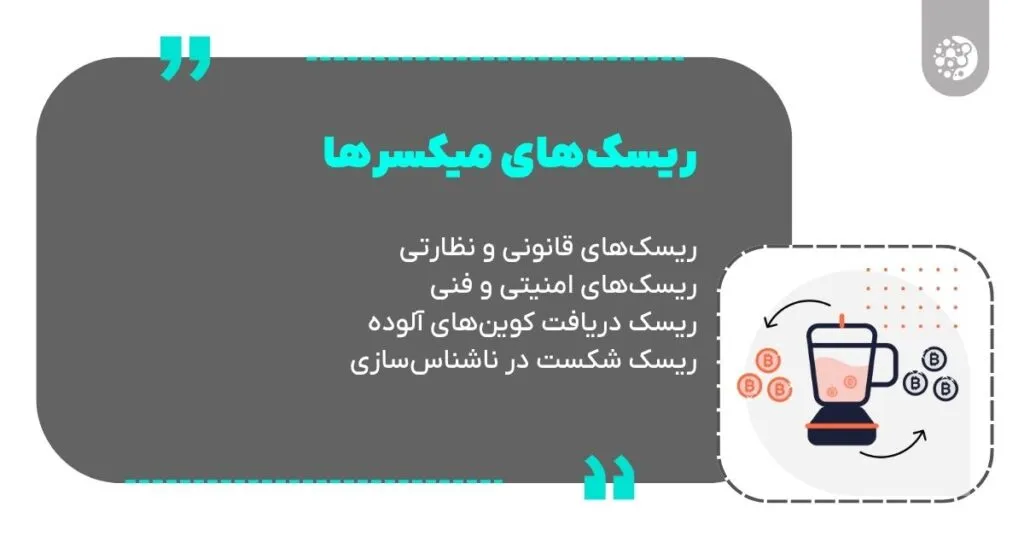
Legal and regulatory risks
This is currently the biggest risk of using mixers. In the United States, the Fincen Network classifies mixers as Money Services Businesses, which requires registration, implementation of anti -money laundering programs (AML) and customer recognition (KYC) and suspicious activity report. Almost none of the general mixers meet these requirements.
The US Treasury Department’s Foreign Asset Control Office (OFAC) has also boycotted all mixing services and has declared their interaction with them illegal for any US person or entity. In Europe, too, the new EU anti -money laundering regulations (AMLR) are explicitly prohibiting the provider of Cryptography asset (CASS) from providing services related to mixers and other privacy reinforcement tools.
There is no specific legislation in our country in this case, but that does not mean being legal. The responsibility of the users’ actions is with them, and if the problem arises, the legal entities will not follow up.
Security and technical risks
One of the security risks associated with mixers is theft. Concentrated mixers can easily steal and disappear users. This is a common fraud known as Exit Scam. In addition, many fraudulent sites replace themselves instead of reputable mixers.
Another security risk is hack. Concentrated mixers hold large pools of digital currency that make them an attractive goal for hackers. A successful hack can lead to the loss of all users’ funds.
And finally, the complex algorithms of these tools can lead to technical risk. Complicated mixing algorithms may fail and lead to loss of funds or sending them to the wrong address.
The risk of receiving contaminated queens
Tainted Coins are queens whose transaction history is related to illegal activities such as theft, Darknet markets or sanctions. If you receive contaminated queen from a mixer, you will inherit their illegal history.
When you try to deposit these queens into a reputable currency exchange, their compatibility software (from companies like Chainalysis) will flag them. This can lead to the following:
- Blocking or closing the immediate closure of your currency exchange account.
- The requirement to prove the origin of funds, which is impossible due to the nature of the mixer.
- Possible investigations by law enforcers and harm to your credit.
The risk of failure in anonymity
Mixers are not anti -clerical. Specialized companies such as Chainalysis and Elliptic have developed complex algorithms for China’s block analysis and tracking of mixed transactions, especially if the mixer is small in volume or the user makes security mistakes.
Also, as we said, a centralized mixer operator can maintain logs that directly connect your input and output transactions. If these logs are seized or revealed, your anonymity will be lost.
Is Bitcoin Mixer Legal?
The answer to this question is complex and dependent on the jurisdiction. The legal status depends strongly on your location. But as we mentioned in the previous sections, most countries in the world do not have a good approach to these tools and are illegally declaring them.
If you use the mixer to hide the source of funds from criminal activities, this is undoubtedly illegal and money laundering. But nowadays, even if you do not have money laundering and abuse, the risk of flagship, seizure of assets, or associated with criminal research is still high.
Bitcoin Mixer Alternatives
Given the risks that the mixers have, in this section we decided to introduce some of the Bitcoin Mixer alternatives.
Privacy Coins (Privacy Coins)
Price Quins are currencies that provide privacy at the protocol level. Monroe (XMR) is a leading currency in the field of Procoecue Quinn and is considered as the golden standard of privacy.
The currency by default uses a combination of Ring Signatures to hide the sender, Stealth addresses to hide the recipient, and Ringct to hide the transaction amount, which makes it really replaceable and inaccurate.
Other famous Price Quins can be mentioned in Zcash and Dash.
Privacy
These are the standard bitcoin wallets that integrate the features of non -indigenous mixing such as Coinjoin.
Wasabi Wallet is a famous and privacy wallet for Bitcoin with coinjoin. Sparrow Wallet is another popular desktop wallet that gives advanced control users to their UTXOs and integrates with coinjoin coordinators.
Other techniques
With the exception of Procozes and wallets, there are other techniques to prevent transactions tracking. One of these techniques is Chain-Hopping. Chain-Hopping means manual transfer of funds between different digital currencies in several currency exchanges, often done using fake or fake identities. This is, of course, a complex and risky method.
Bitcoin’s society has also been thinking of promoting the pursuit of transactions. For example, the Taproot Bitcoin Improvement Plan is an update to the bitcoin network that improves privacy for complex transactions (such as multicolors). This upgrades make multiple transactions from simple payments, though it is not a mixture of mix itself.
Frequently asked questions
The fees are variable, but usually between 0.5% and 5% of the mixed amount. Higher fees sometimes mean more sophisticated mix and privacy.
Coinjoin is a decentralized protocol in which several users work together to create a joint transaction. This technology is decentralized with decentralized mixers. Ordinary concentrated mixers are third -party services that provide your funds, while in coinjoin you maintain your funds.
Yes, this is a risk. Valid currency exchanges use anti -money laundering software to identify contaminated or mixed queens and will block or limit your account if they are identified.
The mixer is an external service used to add privacy to a transparent digital currency such as bitcoin. Price has been put in default into their original protocol and does not require external service.
No. There is no guarantee. China’s block analysis companies are getting better in tracking of mixed transactions and there is always the risk of human error or logging by the operator.
Conclusion
In this article we examined what the bitcoin mixer is and how it works. We then explained the types and applications of these tools, and at the end we took a closer look at their risks and their alternatives.
Mixers are an attractive season in the continuous development of digital currency technology. However, their usefulness has been overshadowed by many risks. Technical challenges, fraud, theft, and severe legal and regulatory risks are part of these risks.
Therefore, we still recommend that when the value of digital currencies is increasing every day, avoid risky measures and take full awareness so as not to threaten your assets.
RCO NEWS